Spike: MODKBEKBJ-358 - Investigate OKAPI request routing implementation
MODKBEKBJ-358 - Getting issue details... STATUS
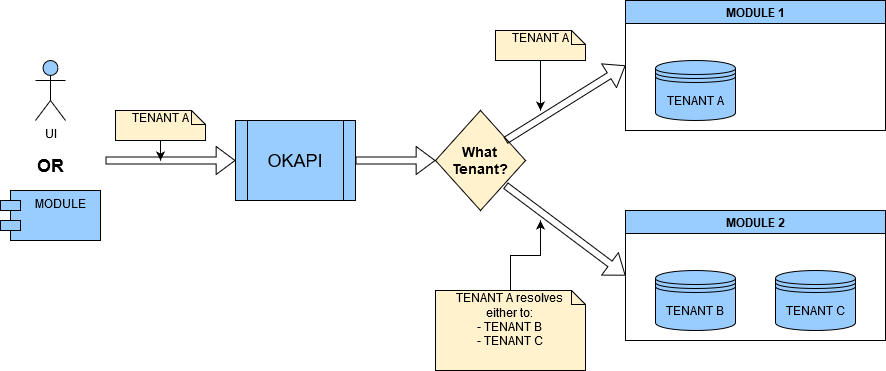
Multi-tenant context execution problem
The system is aware of 3 tenants:
- Tenant A
- Tenant B
- Tenant C
There is also some relation between the tenants so that in some cases Tenant A can be replaced with Tenant B and in another cases with Tenant C.
Module 1 can be executed in the context of Tenant A only
Module 2 can be executed either in the context of Tenant B or Tenant C but not Tenant A
To execute Modules in proper context there has to be a component to resolve the correct tenant before the request gets to the modules.
Module characteristics important for request processing
Module characteristics defined in ModuleDescriptor-template.json. Here is the module descriptor from mod-authtoken:
Modules can declare two ways to handle a request:
- handlers
- filters
There should be exactly one handler for each path. That will be of request-response type by default.
Each request may be passed through one or more filters. Filters have a phase attribute which determines the order in which filters are applied.
At the moment we have three phases defined:
- auth will be invoked first. It is used for checking the
X-Okapi-Token, and permissions. - pre will be invoked just before the handler. It is intended for logging and reporting all requests.
- post will be invoked just after the handler. It is intended for logging and reporting all responses.
The type attribute in the RoutingEntry in the ModuleDescription controls how the request is passed to the filters and handlers, and how the responses are processed. Currently, the following types supported:
- headers -- The module is interested in headers/parameters only, and it can inspect them and perform an action based on the presence/absence of headers/parameters and their corresponding value. The module is not expected to return any entity in the response, but only a status code to control the further chain of execution or, in the case of an error, an immediate termination. The module may return certain response headers that will be merged into the complete response header list according to the header manipulation rules below.
- request-only -- The module is interested in the full client request: header/parameters and the entity body attached to the request. The headers returned including the response code affects further processing but the response body is ignored. Note that type request-only Okapi will buffer an incoming request body (POST presumably) into memory. This does not scale for large import(s) or the like. Use request-log instead if the response may be ignored.
- request-response -- The module is interested in both headers/parameters and the request body. It is also expected that the module will return an entity in the response. This may be e.g. a modified request body, in which case the module acts as a filter. The returned response may then be forwarded on to the subsequent modules as the new request body. Again, the chain of processing or termination is controlled via the response status codes, and the response headers are merged back into the complete response using the rules described below.
- redirect -- The module does not serve this path directly, but redirects the request to some other path, served by some other module. This is intended as a mechanism for piling more complex modules on top of simpler implementations, for example, a module to edit and list users could be extended by a module that manages users and passwords. It would have actual code to handle creating and updating users, but could redirect requests to list and get users to the simpler user module. If a handler (or a filter) is marked as a redirect, it must also have a redirectPath to tell where to redirect to.
- request-log -- The module is interested in the full client request: header/parameters and the entity body attached to the request. This is similar to request-only but the entire response, including headers and response code, is ignored by Okapi. This type appeared in Okapi version 2.23.0.
- request-response-1.0 -- This is like request-response, but makes Okapi read the full body before POSTing to the module so that Content-Length is set and chunked encoding is disabled. This is useful for modules that have trouble dealing with chunked encoding or require getting content length before inspecting. This type appeared in Okapi 2.5.0.
Handlers can define one or more permissions required to be able to execute the handler. The permissions can come from two sources: either they are granted for the user, or they are granted for a module. See a simplified version of module descriptor from mod-notes below. "permissionsRequired" attribute defines user permissions, "modulePermissions" attribute defines permissions granted to the module specifically during the particular request handling
OKAPI request processing
- OKAPI receives a request with URI address
- It builds a list of modules that serve the request, and that are enabled for the tenant. The modules are sorted according to their configuration in ModuleDescriptors
- usually, the list consists of two modules
- authentication and authorization module (mod-authtoken)
- target module to handle the request (like mod-inventory, mod-orders, mod-kb-ebsco-java)
- usually, the list consists of two modules
- OKAPI combines all required permissions from modules involved in the call
- OKAPI starts sending requests for the modules. For each module in its pipeline list, it
- Checks where the module is running (which node, which port)
- Passes the original HTTP request to the module, with additional headers
- When the module response arrives, Okapi checks if it was an OK response. If not, it will return the error response to the caller, and abort all processing.
- When Okapi has processed all modules in its list, it returns the last response to who ever called it.
Authorization
Each call to a business module has to be authorized by Auth module (mod-authtoken).
Authorization includes the following steps (the steps are actually might varу depending on the call context):
- Checks that the request has an
X-Okapi-Tenantheader - Checks if there is an
X-Okapi-Tokenheader. If not, it creates one. - If there is an
X-Okapi-Token, it verifies it. - Validates that user is active: user with userId obtained from the request has "active" attribute equal to true
- Tests that user has all the necessary permission to call the module
If any of the validation tests failed then the whole authorization process failed and the request processing is aborted abnormally.
Request flow samples
The samples provided below show two common cases of request flow:
- request is processed by a single module only (Simple Case)
- request involves several modules in the processing (Advanced Case)
- usually, there is a main module or orchestrator which receives the initial request and then delegates some work to other modules. The response is also returned to the caller by the orchestrator.
Modules involved in sample flows:
- OKAPI (okapi)
- Auth-Token (mod-authtoken)
- Users (mod-users)
- Permissions (mod-permissions)
- Notes (mod-notes)
- Configuration (mod-configuration)
OKAPI_1/OKAPI_2 and Auth-Token_1/Auth-Token_1 are the same components OKAPI and Auth_Token respectively. They are duplicated just for the convenience of showing a flow on the diagrams.
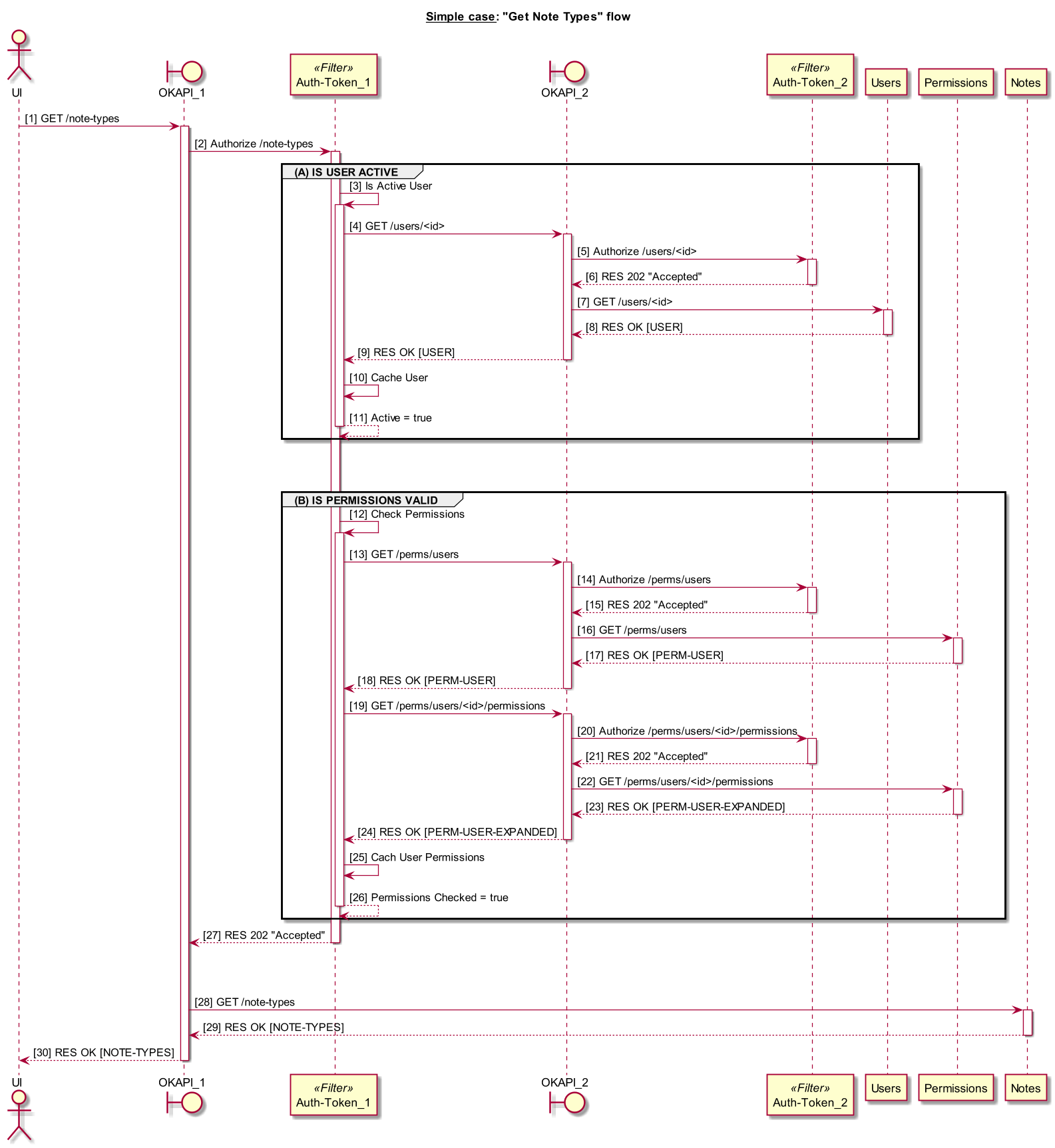
Simple Case: a single business module is called
Use Case:
Retrieve a list of "note types" defined in the system
Main Steps:
- UI sends GET /note-types request to OKAPI
- The request is authorized by Auth module (Auth-Token)
- user issued the request verified to be an active one - (A) IS USER ACTIVE
- user permissions checked - (B) ARE PERMISSIONS VALID
- OKAPI sends the request to Notes module
- Notes module retrieves the list types and replies back to OKAPI which in turns returns the list to UI
OKAPI log: okapi-get-note-types.log
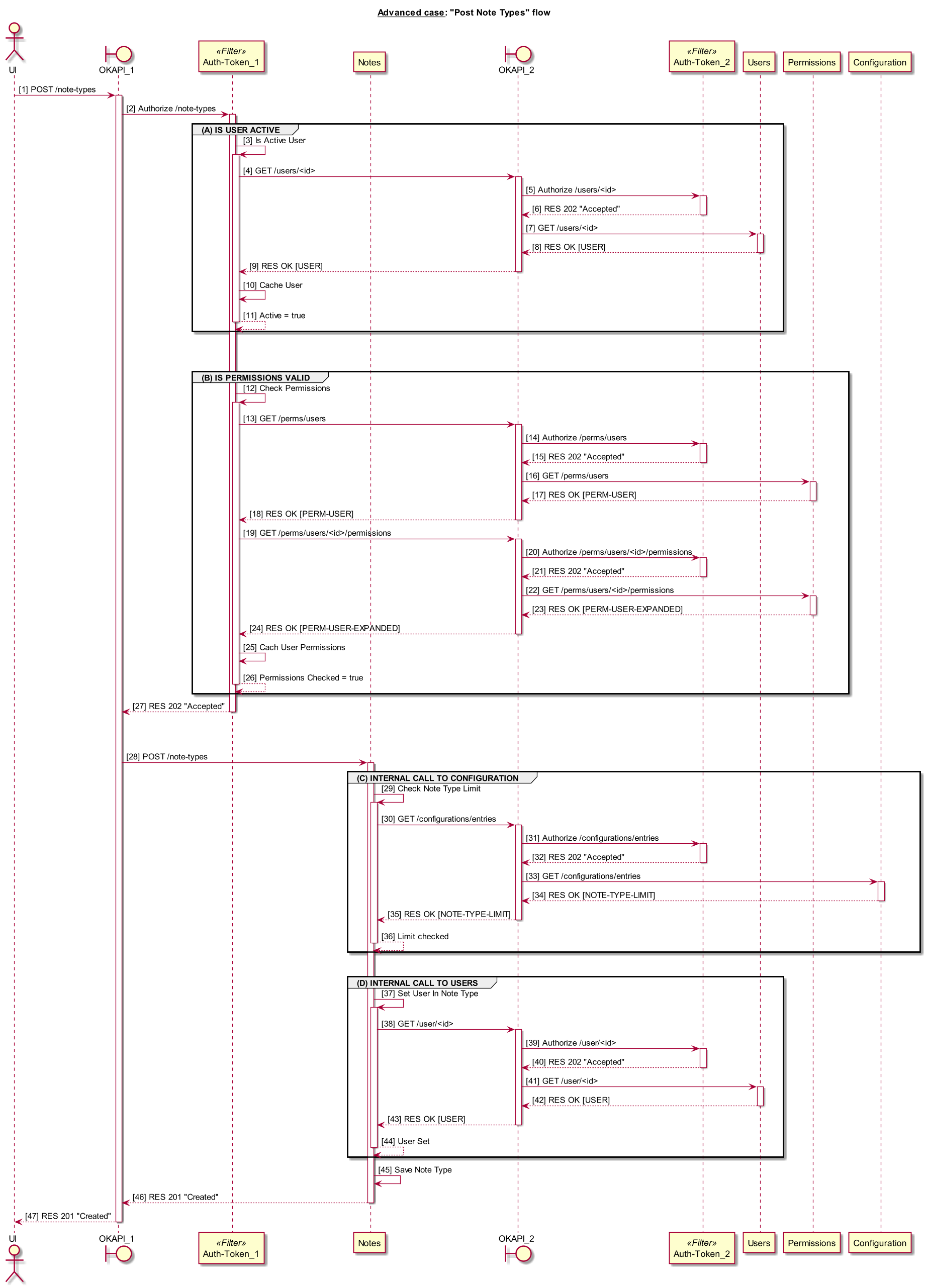
Advanced Case: several business modules are called internally
Use Case:
Create a new "note types".
Main Steps:
- UI sends POST /note-types request with new note type details to OKAPI
- The request is authorized by Auth module (Auth-Token)
- user issued the request verified to be an active one - (A) IS USER ACTIVE
- user permissions checked - (B) ARE PERMISSIONS VALID
- OKAPI sends the request to Notes module
- Notes module receives the request and processes it as follows:
- calls Configuration module to get the maximum number of note types allowed in the system - (C) INTERNAL CALL TO CONFIGURATION
- configuration request passes OKAPI and Auth as usual and gets to Configuration module which retrieves the limit and sends it back Notes module
- the maximum number of types limitation applied, if successful the process continues
- new note type has to be populated with user creator details, so Notes calls Users to get the details of the current user - (D) INTERNAL CALL TO USERS
- user request passes OKAPI and Auth as usual and gets to User module which retrieves user by id and sends it back Notes module
- new note type populated with user creator details and saved
- "Created" response returned to UI
- calls Configuration module to get the maximum number of note types allowed in the system - (C) INTERNAL CALL TO CONFIGURATION
OKAPI log: okapi-post-note-type.log
Summary
- tenant resolution can be integrated into the request flow as filter at "pre" phase
- create a POC to test the approach with tenant resolution module acts as a filter
- POC should also include some basic logic to support Consortia business requirements at least for
- mod-kb-ebsco-java and
- mod-notes
- examine any possible issues with replaced tenant
- in particular the potential difference between tenant value in x-okapi-tenant and x-okapi-token headers
- POC should also include some basic logic to support Consortia business requirements at least for
Reference information:
- Okapi Guide and Reference
- Okapi Security Model
- Sample responses of calls issued during authorization
- Diagram source files
- Simple case: get-notes.puml
- Advanced case: post-notes.puml