Snyk
FOLIO uses Snyk to scan for security vulnerabilities.
We collect, triage and maintain the results in the https://app.snyk.io/org/folio-org organisation that is restricted to the FOLIO Security Team.
Free Plan
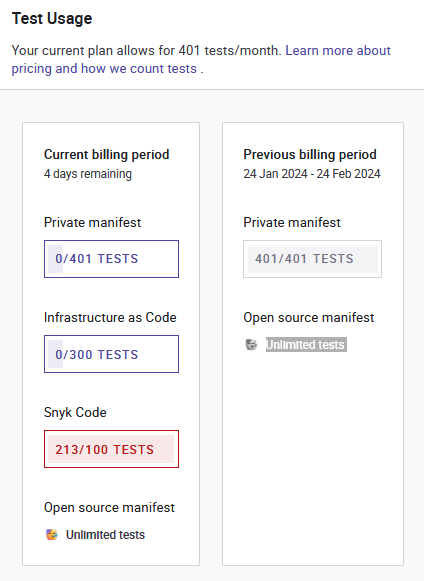
FOLIO is on the free plan and has this scan limitations (see screenshot in the rightmost column):
| public repositories | private repositories | FOLIO's usage of Snyk Tests March/February 2024 | |
|---|---|---|---|
| Open Source (maven/npm/... dependencies) via Web UI | unlimited | 401 tests/month | |
| Code (SAST of source code) | 100 tests/month | ||
| Infrastructure/IaC (Kubernetes/Helm/AWS/Azure/...) | 300 tests/month | ||
| Container (Docker/OCI) | 100 tests/month | ||
The unlimited "Open Source" scans are scheduled daily, all other scans are scheduled weekly: https://app.snyk.io/org/folio-org/manage/usage
Click "Retest now" to trigger an immediate scan of the main/master branch of the repository.
"GitHub" Scan
Pros:
- Unlimited dependency scans (maven, npm, ...) of public repositories.
- Any number of branches per repository: Snyk picks up all changes for all imported branches and reports issues for all of them.
- Better priorization by reachable vulnerabilities heuristics.
- Fixed: Some time ago it didn't support <dependencyManagement> of pom.xml files so the CLI had been used. This has been fixed.
Con:
- On import it only imports the default branch (usually master or main). Changing the default branch for a few seconds allows to import any branch. After import snyk doesn't care whether a branch is still the default branch.
"CLI" Scan
Pro: Sometimes it might work for reporitories where the Snyk "GitHub" scan doesn't work but currently all those cases have been fixed by the Snyk people.
Cons:
- Counts to the private repository limit that has only a few CLI scans available in our free Snyk plan, therefore we don't use this.
The SNYK_TOKEN is needed, it's available as a secret for GitHub Actions in all https://github.com/folio-org repositories.
- To automatically run the Snyk CLI on a merge or a pull request a CI process like Jenkins or GitHub Action is needed to start it.
- Reachable vulnerability analysis for better priorization via the Snyk CLI is not currently supported.
Ignored
Use these texts as a comment when setting a false positive report to "ignore".
CVE-2022-23218 "deprecated compatibility function svcunix_create in the sunrpc module of the GNU C Library":
Debian provides the svcunix_create function, but no Debian package uses it: https://codesearch.debian.net/search?q=svcunix_create&literal=1 Debian doesn't provide fixes for stretch/buster/bullseye: https://security-tracker.debian.org/tracker/CVE-2022-23218 FOLIO doesn't use svcunix_create: https://github.com/search?q=org%3Afolio-org+svcunix_create- CVE-2022-23219 "deprecated compatibility function clnt_create in the sunrpc module of the GNU C Library":
Used by many Debian packages: https://codesearch.debian.net/search?q=%5Cbclnt_create%5Cb&literal=0 However, Debian by default builds packages with stack protection enabled and therefore is not affected by this issues, rates it "Minor issue" and doesn't provide fixes for stretch/buster/bullseye: https://security-tracker.debian.org/tracker/CVE-2022-23219 FOLIO doesn't use clnt_create: https://github.com/search?q=org%3Afolio-org+clnt_create
Deactivated
- https://github.com/folio-org/NCIP2-Toolkit because it is used to generate jar files, but only a few are used by mod-ncip, and Snyk tests the used jar files when testing mod-ncip. NCIP2-Toolkit contains 87 critical vulnerabilities in the Dockerfile and several hundred vulnerabilities in total. However, the Snyk "Code analysis" of NCIP2-Toolkit is still enabled because it can only run on source code, not on the jar used in mod-ncip.
Import all folio-org
Developers add new GitHub repositories to https://github.com/folio-org, and add new files like Dockerfile or package.json or new pom.xml subprojects to existing repositories that require a new snyk project. Therefore we need to regularly (re)import all GitHub repositories.
Steps:
- Click "Add project" "GitHub"
- Click "Show more" until all repositories are listed
- Select all by clicking the box next to "folio-org"
- Deselect all archived repositories, they have the archive symbol next to them.
- Deselect NCIP2-Toolkit, see above to learn why.
- Click "Add selected repositories"
The last date when we have imported all folio-org repositories: 2024-10-21
Import others
Some projects from outside the GitHub folio-org organisation are relevant to FOLIO and are imported into the folio-org Snyk project to monitor them alongside the regular.
https://github.com/k-int/web-toolkit-ce is used by ERM modules: https://github.com/search?q=org%3Afolio-org+web-toolkit-ce&type=code
https://gitlab.com/knowledge-integration/folio/grails-okapi is used by ERM modules: https://github.com/search?q=org%3Afolio-org+grails-okapi&type=code
https://github.com/zonkyio/embedded-database-spring-test is io.zonky.test:embedded-database-spring-test that is used by a few FOLIO repositories: https://github.com/search?q=org%3Afolio-org+embedded-database-spring-test&type=code
https://github.com/indexdata/localindices is the legacy harvester to work with FOLIO: https://github.com/indexdata/localindices/search?q=folio
Manual dependency scan
Developers may want to check the dependencies locally before commiting the change for a pull request branch.
maven
mvn dependency:tree -Dverbose -Dincludes=org.springframework:spring-web
If you keep the colon : you can omit the groupId:
mvn dependency:tree -Dverbose -Dincludes=:spring-web
For repeated use you may create ~/bin/dep with this content:
mvn dependency:tree -Dverbose -Dincludes=$1
gradle
cd service./gradlew dependencies