Tenants topology
Deployment steps
Create central and institutional tenants
To perform multi tenancy consortia setup lets create 3 tenants with ids: consortium, university, college
Tenant creation
For tenants creation the standard okapi tenant creating endpoint should be used: POST /_/proxy/tenants
We need to create new host with UI only for the central tenant.
Only single host need to be deployed
Consortium users will use only the central tenant DNS host for all operations, if users need to apply operations from the context of another institutional tenant - they can switch active affiliation in the header.
Enable modules on tenants
We should follow the standard procedure of enabling tenants from install.json and enable all desired modules except one UI module folio_consortia-settings that should be enabled only in the consortium central tenant
Differences between central and institutional tenants
Module folio_consortia-settings should be enabled only in consortium central tenant
Configure tenants
Reference data should be created on both central and institutional tenants, sample data - only on central consortium tenant. Reset password link, SMTP for sending emails should be configured on all tenants. Separate admin users in each tenant can be created to apply all this configuration.
Create admin user in the central tenant
For Consortia setup it is required to create admin user in the central consortium tenant. For other tenants shadow admin users with required set of permissions will be created automatically during Configure consortium tenants step.
This admin user should contain all existing permissions that admin users currently have for our common envs plus 2 additional:
- consortia.consortium.item.post
- consortia.tenants.item.post
Endpoint to create admin user
Configure consortium tenants
Tenant context
Create consortium record
Validation requirements:
- Only 1 consortium record should exist across cluster. adding more is prohibited
Request to create consortium record:
POST /consortia HTTP/1.1
X-Okapi-Tenant: consortium
X-Okapi-Token: <JWT>
Content-Type: application/json
{
"id": "a617d446-4c00-4f8f-bcd4-5beacbccef67",
"name": "Mobius"
}
Create consortium tenants
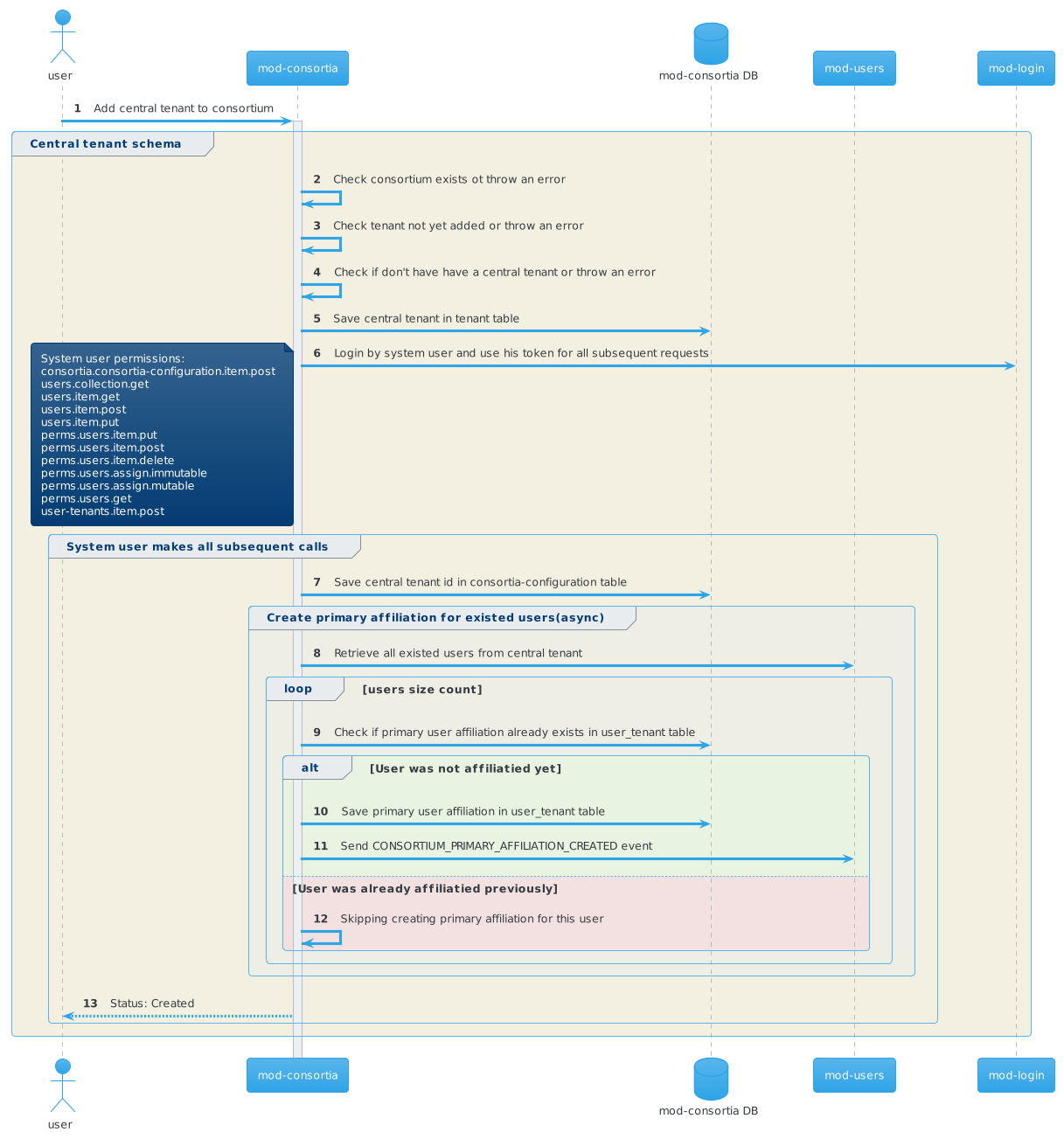
Actions performed under the hood of invoiking POST /consortia/{consortiumId}/tenants:
- Store central tenant id in the consortia_settings table of the desired tenant
- Perform primary affiliation creating for all existing users asynchronously
- Invoke /user-tenant to store dummy user
Validation rules:
- Consortium record should be created before adding tenant
- Name and code fields should be unique
- Name min length - 2, max length - 150
- Code min length - 3, max length - 3, regex pattern - '^[a-zA-Z0-9]*$'
- Tenant should not be existed already
- Central tenant should be added firstly
- Adding tenant when some another tenant has setupStatus = "IN_PROGRESS" is forbidden
Add central tenant to the consortium
Request to create central consortium tenant:
POST /consortia/a617d446-4c00-4f8f-bcd4-5beacbccef67/tenants HTTP/1.1
X-Okapi-Tenant: consortium
X-Okapi-Token: <JWT>
Content-Type: application/json
{
"id": "consortium",
"name": "Central office",
"code": "MCO",
"isCentral": true
}
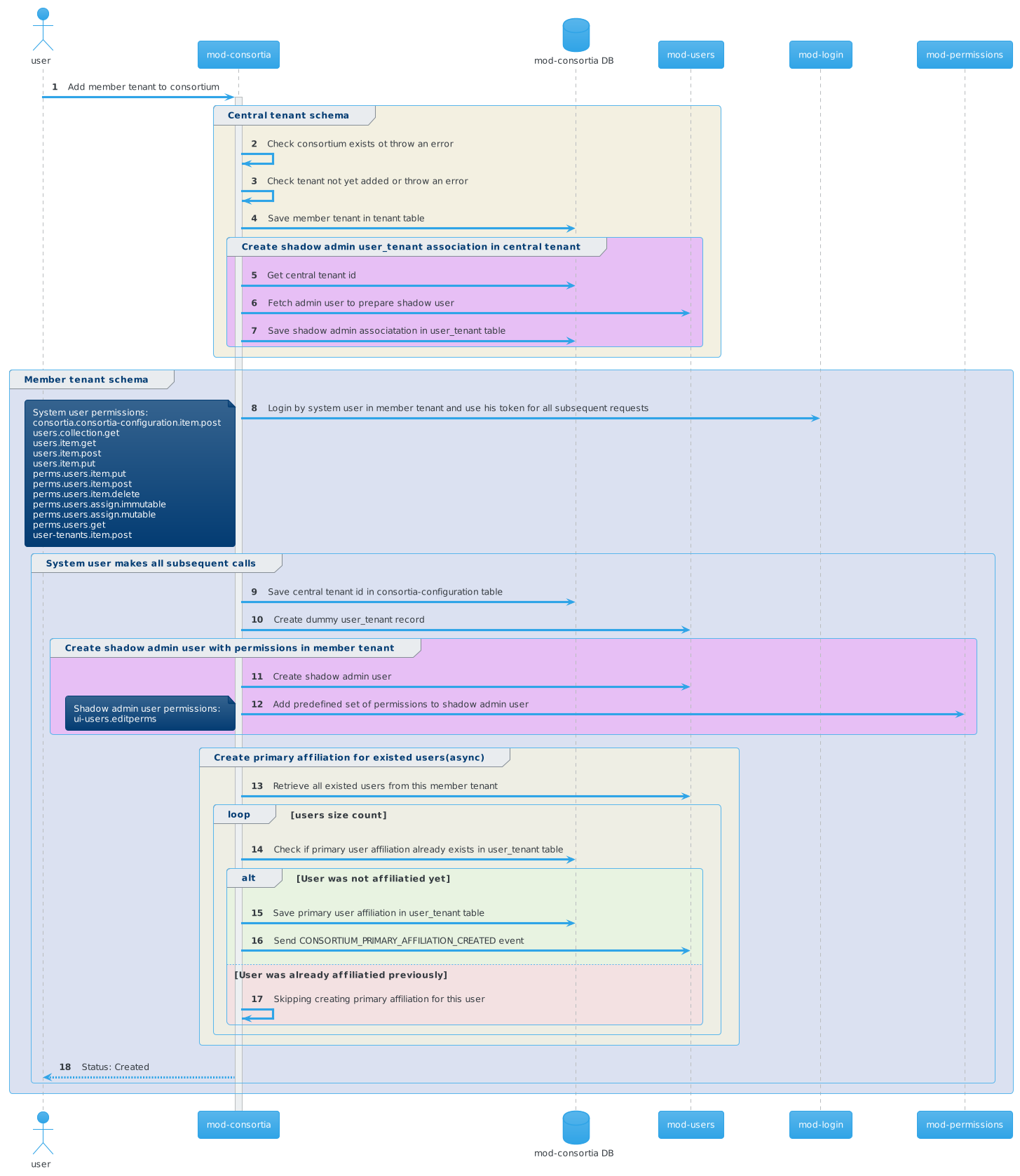
Add institutional tenants to the consortium
New request param adminUserId added
Pay attenation that new request parameter adminUserId has beed added. It used to create shadow admin user in the desired teanant with predefined set of permissions.
It should be adminUserId for admin user from the central Tenant
Request to create University tenant:
POST /consortia/a617d446-4c00-4f8f-bcd4-5beacbccef67/tenants?adminUserId=b20c4397-ad56-479f-891a-30a5a471f24b HTTP/1.1
X-Okapi-Tenant: consortium
X-Okapi-Token: <JWT>
Content-Type: application/json
{
"id": "university",
"name": "University",
"code": "UNI",
"isCentral": false
}
Request to create College tenant:
POST /consortia/a617d446-4c00-4f8f-bcd4-5beacbccef67/tenants?adminUserId=b20c4397-ad56-479f-891a-30a5a471f24b HTTP/1.1
X-Okapi-Tenant: consortium
X-Okapi-Token: <JWT>
Content-Type: application/json
{
"id": "college",
"name": "College",
"code": "COL",
"isCentral": false
}
Order to add tenants to the consortium
Sequential order to add tenants to the consortium should be used, because under the hood we are making operations to create users in other tenants and simultaneously have an async operation to migrate existing users in current tenant.
Firstly, an automation job should create a central tenant and after this - all member tenants.
To control the tenant setup state we have a field 'setupStatus' in tenant response body with allowed values: "IN_PROGRESS", "COMPLETED", "COMPLETED_WITH_ERRORS", "FAILED".
Automation deployment job should make polling of GET /consortia/{{consortiumId}}/tenants/{{tenantId}} endpoint until COMPLETED or COMPLETED_WITH_ERRORS status.
Poll interval can be chosen as 10 sec for example.
mod-consortia prevents adding new tenant when some tenant in DB has setupStatus with "IN_PROGRESS" value.
Here is description of all possible statuses:
| Status | Description |
|---|---|
| IN_PROGRESS | Adding tenant to the consortium is in progress, new POST requests to add another tenants is prohibited |
| COMPLETED | Adding tenant is completed, can start adding next tenant |
| COMPLETED_WITH_ERRORS | Tenant has been added, but not all existing users have been affiliated though the mod-consortia pipeline, pipeline can continue adding another tenants. To repeat the process of syncing primary affiliations for existing users /sync-primary-affiliations can be invoked. |
| FAILED | Some unexpected error occurred, the tenant has not been added to the consortium or not all existing users have been affiliated though the mod-consortia pipeline. The preferred way here is to stop executing automation pipeline and investigate reasons for these errors via logs |
User type is required in ECS mode
On some of the customers it is possible to have more than 1.3 million of patron users, ECS does not need to process all of them through a consortium pipeline, because patron users can not and should not login to consortia.
So 'type' field for user is required now in ECS mode, for non ECS it is optional.
This change brings 2 benefits:
- General performance of ECS increases because ECS logic will work with thousands of staff/system users instead of millions of patron users
- A clear way to distinguish user types in Folio appears
Possible user types:
| № | User type | Description | Processed by consortia pipeline? |
|---|---|---|---|
| 1 | staff | Regular staff user | Yes |
| 2 | patron | Regular parton user | No |
| 3 | system | User created by internal modules usage | Yes |
| 4 | shadow | Shadow user created when adding affiliation to the desired tenant | No (kafka messages will be send only for real users, but not for shadow) |
How to deal with existing users
What is going on during this process of migrating existing users?
When adding tenant to the consortium the process of migrating existing users through consortia pipeline started in scope of each:
- primary affiliation and affiliation in central tenant(if user is from member tenant) with shadow users created
- user-tenants table in mod-users populated in central tenant that allows existing users to login in ECS
Conclusion: users processed by consortia pipeline can login and affiliations will be manageable in ECS mode
When to migrate existing users, before or after enabling ECS mode?
Before enabling ECS mode
Process of migration of existing users is added to process some system or admin users by ECS pipeline or in case when ECS mode is enabled on an already existing tenant that already has users with populated 'type' field.
Query used to fetch existing users used by mod-consortia: (cql.allRecords=1 NOT type =\"patron\" NOT type = \"dcb\" ). So with this query all users without 'type' field populated or if 'type' not equals to 'patron' or 'dcb' will be migrated.
One important note to take in mind - that if for example 1.5 mil of patron users were created without populating 'type'='patron' when ECS still not enabled - all 1.5 mil will be migrated that is not desired behavior,
because validation that 'type' is required field enabled only when ECS mode enabled and ECS needs to skip processing users in the pipeline.
After enabling ECS mode
If we have a choice - better to enable ECS mode for tenant and after start creating/migrating users that would be processed by mod-consortia via kafka domain events sent by mod-users.
In this case nobody can create users without populating the 'type' field because validation is enabled in ECS mode. For some customer we can have more than 1.5 mil of patron user and only couple thousands of staff users,
so in this case we can guarantee that mod-consortia will process only these thousands of staff users and exclude millions of patrons.
Conclusion: better to migrate existing users after enabling ECS mode for tenant
Do we need to adjust our existing admin users to populate type='staff'
Let's start from system users, all repositories were updated to create new system users with type='system' and also migration script is written in mod-users to add type='system' for all existing system users.
So for system users no actions required.
For admin users it is better to do but not required. We suggest adding type='staff' to not confuse why some users existed without 'type' populated in ECS mode where this type field is required.
Also some new features like filtering by user type in Users App will not take in consideration such users.
But even without populating 'type' for admin users - mod-consortia will pick up such users and process by ECS pipeline during migrate existing users process when adding tenant to the consortium,
because this process takes users even without 'type' populated.
Conclusion: for 'system' no action needed, for common admin users - better to add type='staff'
BE Modules modified for supporting consortia functionality
Thunderjet team
| № | Module | Changes made | Hosting changes |
|---|---|---|---|
| 1 | mod-consortia |
| - |
| 2 | mod-users |
| - |
| 3 | mod-users-bl |
| - |
| 4 | mod-login |
| - |
| 5 | mod-authtoken |
| System param(declared in JAVA_OPTS) should be added: -Dallow.cross.tenant.requests=true RANCHER-903 - Getting issue details... STATUS |
Firebird team
| № | Module | Changes made | Hosting changes |
|---|---|---|---|
| 1 | mod-oai-pmh |
| - |
| 2 | edge-oai-pmh |
| permissions + users, To be defined |
| 3 | mod-data-export |
| - |
Folijet team
| № | Module | Changes made | Hosting changes |
|---|---|---|---|
| 1 | mod-inventory |
| - |
| 2 | mod-inventory-storage |
| - |
| 3 | mod-source-record-manager |
| - |
| 4 | mod-source-record-storage |
| - |
Spitfire team
| № | Module | Changes made | Hosting changes |
|---|---|---|---|
| 1 | mod-search |
| Tenant paramenter centralTenantId should be added(during tenant enabling) RANCHER-898 - Getting issue details... STATUS |
| 2 | mod-entities-links |
| - |
Volaris team
| № | Module | Changes made | Hosting changes |
|---|---|---|---|
| 1 | edge-patron | Provide a consortia-level access point/mechanism for retrieving patron data | - |
| 2 | edge-common | Support Consortium Authentication & Routing | - |
Issues found during consortia env setup
| № | Issue description | Related tickets |
|---|---|---|
| 1 | Simaultainious adding tenants to consortia can cause concurrent issues | MODCON-73 - Getting issue details... STATUS RANCHER-893 - Getting issue details... STATUS |