Date
...
| Name | Present |
|---|---|
| Y | |
| Y | |
| Y | |
| Y | |
| Y | |
| N | |
| Y | |
| N | |
Discussion items
| Time | Item | Who | Notes | ||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5 min | mod-configuration - should it be deprecated or not? | mod-configuration has been discussed on the development channel recently. Developers like it because they can simply drop variables to the /configurations/entries API. Simply use the "configuration.*" permission shared by all modules and you are done. No need to add schema validation, no need to add dedicated permissions, no need to add a dedicated API.
Team decided we want to have this as a RFC. Target should be to have this implemented within Nolana. Could discuss in your meetings while the RFC process moves on.
Today:
| |||||||||||||||||
| 0 min | Kafka security | Team | The topic of Kafka security was raised as part of a conversation at the TC yesterday. The Security Team should be aware of this and probably should weigh in on the topic, or even generate proposals if we have ideas for how to solve the problem.
Today:
| ||||||||||||||||
| 5 min | OWASP/SNYK | Team |
Today:
| ||||||||||||||||
| 5 min | Cumulative upload problem | Team |
Today:
| ||||||||||||||||
| 5 min | STCOR-395 "refactor login form to avoid using any form framework whatsoever" | All |
Today:
| ||||||||||||||||
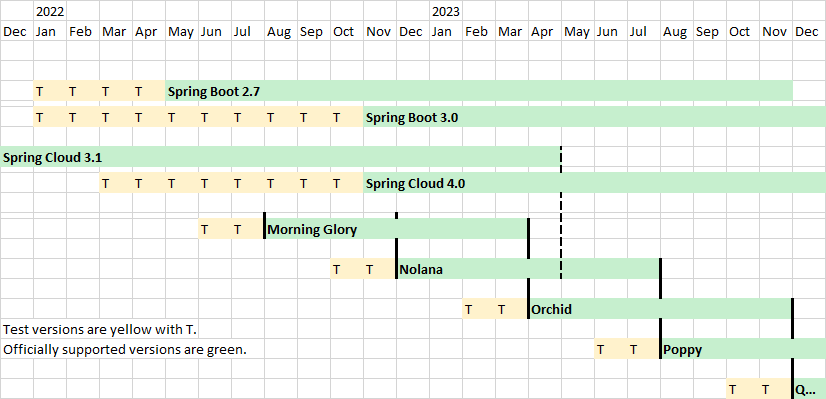
| 0 min | Spring versions and the Official Supported Technologies pages | I've added versions for the Spring components to the Officially Supported Technologies list. For Orchid it's easy: https://wiki.folio.org/display/TC/OrchidFor Nolana it's more complicated: https://wiki.folio.org/display/TC/NolanaThe OSS support of several Spring components ends in May 2023. This is more than three months before the end of the Nolana support period that end in August or September 2023. The next minor version of those Spring components will be released in November 2022, this is during Nolana bug fest. We need to bump to this next minor version and release a bug fix for all affected FOLIO Spring libraries and FOLIO modules in November 2022.Running unsupported Spring components is a security risk. If there is a security issue in a supported Spring component we simply can bump the patch version, no risk. If there is a security issue in an unsupported Spring component we don't get notified because it's unsupported, and if we know of an issue we need to bump the minor version, this comes with some risk. Bumping the minor version as early as possible gives more testing time and is less risky. We can discuss this today.
Today:
| |||||||||||||||||
| 5 min | Core-platform auth work |
Today:
| |||||||||||||||||
| skipped | Cyber Resilience Act | Team | I raised this with the TC but we should also be aware... https://blog.nlnetlabs.nl/open-source-software-vs-the-cyber-resilience-act/ https://digital-strategy.ec.europa.eu/en/library/cyber-resilience-act | ||||||||||||||||
* | Review the Kanban board. | Team |
...